50% Of All Work from Home Employees Are Ignoring Cybersecurity Protocols
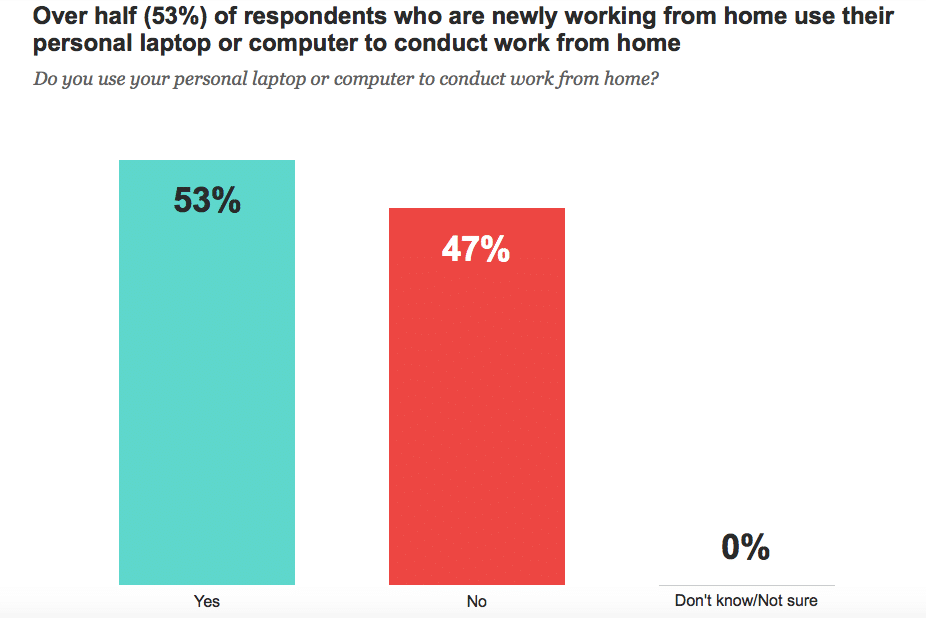
According to a recent study, more than half of work from home employees are putting their organizations at risks for a cybersecurity attack by being lax about security protocols. With an increase of almost a third of the country working from home due to covid-19, the amount of risk for organizations to suffer an online […]
50% Of All Work from Home Employees Are Ignoring Cybersecurity Protocols Read More »