
It does not matter if you are building a VoIP system for a multi-location enterprise or a five person law office. Securing your network is paramount. VoIP fraud, or more generally toll fraud, can cost businesses a lot of money. Here is a few of the common attacks and how to mitigate them.
The Firewall.
A lot of VoIP systems have IP access restrictions and rate limiting features now-a-days. With that said, you should not rely on those alone. The first line of defense is the firewall at the customer’s network edge. You should have rules in place limiting who can access the VoIP system on port 5060. Many firewalls will have SIP ALG’s (Application Layer Gateways) that attempt to manage NAT translation for SIP traffic. I have found these to be problematic in many cases. At N2Net, we use the Edgewater Networks Edgemarc device to both manage NAT and provide security to VoIP systems behind it.
Brute Forcing SIP Extension Attacks.
There are automated attacks today that are designed to repeatedly attempt to register a SIP extension using common usernames and easy-to-guess passwords. Aside from a properly configured firewall and registration rate limiting, the best way to defend against such attacks is to ensure you are using a strong SIP password for your end point. A common mistake is to use the extension number as the username.
Sending Unsolicited International Calls.
Another brute force method is to send calls to international destinations. The attackers will send SIP INVITE messages to your switch in hopes that the number will match and the call will be placed. This will increase your phone bill very quickly. At N2Net, we use an Edgemarc device at the edge of the customer’s network to ensure we are only accepting calls from trusted sources. However, if you do not have a need for international calls, be sure to not allow them to be made from your PBX. Below is how you configure the Edgemarc to do so.
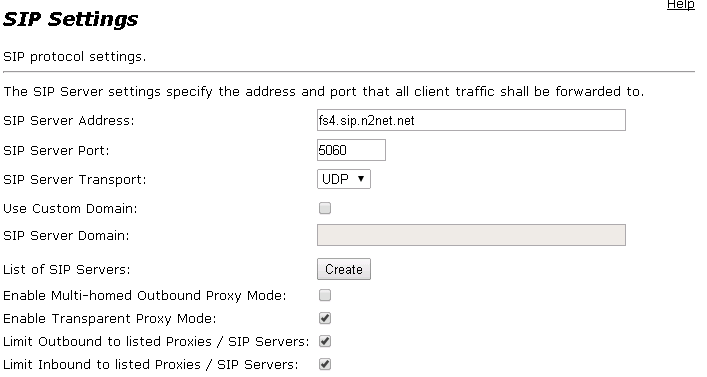
The “Limit Inbound to listed Proxies” setting ensures that the Edgemarc will only accept SIP traffic from the SIP server listed.
In a later article, we will talk about specific Edgemarc setup utilizing the ALG and our SIP service.
